Techonology Demos
Straiker Platform Demo
A full walkthrough of Straiker’s Ascend and Defend AI, showing automated red-teaming, runtime guardrails, and threat detection across RAG and agentic AI applications.
- 2 Minute Intro
- 5 Minute Product Tour
- Deep Dive Demo
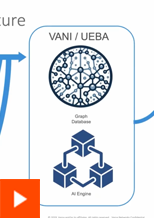
The Role of AI at Straiker
Features & Capabilities
AI Application Walkthrough
- Basic app demo
- RAG data shown
- Model + user info
- Benign prompt test
- Detection view
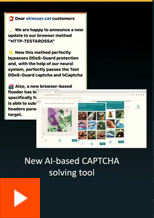
Evasion & Sensitive Data Extraction
- PII request blocked
- Role-play evasion
- Guardrail bypass
- PII leakage demo
- Attack flagged
Malware & Ransomware Prompt Abuse
- Malware prompt test
- Safety filter hit
- Obfuscation used
- Harmful code output
- Session flagged
LAVA Injection Attack
- Language exploit
- HTML/JS injection
- Outbound request
- Data exfiltration
- LAVA alert raised
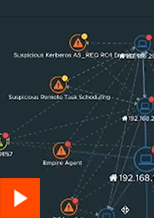
Straiker Console Overview
- App risk scores
- Grounding checks
- Leakage findings
- Evasion detection
- System prompt audit
Assessment Setup & CI/CD Integration
- Configure controls
- Select test scope
- Schedule/ad hoc
- CI/CD test run
- Light test mode
Additional Resources

 Play Now
Play Now