Analyst Briefing
Anton Chuvakin
Industry Analyst
Google
David Goldschlag
CEO
Aembit
Anton Chuvakin
Industry Analyst
Google
David Goldschlag
CEO
Aembit
David explains how workload identity extends IAM beyond humans to software and AI agents, enabling zero trust, least-privilege access while authenticating machines, manages policies, and secures enterprise data at scale.
Viewpoint: IAM for Agentic AI
Apurva Davé
Chief of Strategy & Marketing
Aembit
Apurva explains how Aembit secures AI agents by replacing hardcoded secrets with identity based, short lived credentials while enforcing policy driven, auditable, zero trust access so teams can safely scale generative AI across sensitive systems.
Secrets Bad, Identity Good: Understanding Workload IAM
Apurva Davé
Chief of Strategy & Marketing
Aembit
A review of how Workload IAM secures machine-to-machine access by replacing static credentials with identity based, zero trust controls while automating access for AI agents, enforcing policies at runtime, and eliminates secret sprawl for safer, scalable enterprise operations.
Technology Demo
Aembit Platform
This demo shows how Aembit allows you to define and enforce access policies between NHIs in and across multiple environments.
- 2 Minute Overview
- 5 Minute Quick Tour
- Deep Dive Platform Demo
Capabilities Demos
Dev view
- Intro
- GitLab pipeline
- ai_agent.sh
- Code without Auth
Aembit Cloud platform
- Intro
- Cloud-based, multi-tenant SaaS
- SSO
- Dashboard tour
Policies
- Overview
- Quick tour
- End to end comms supported
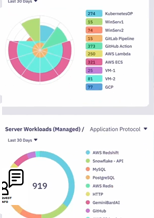
Client & server workloads
- Overview
- Defining workloads
- Two examples: Globex and GitLab
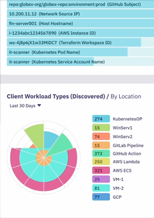
Verifying client workload identities
- Intro: Attestations
- Show Trust Providers
Enabling Zero Trust checks for workloads
- Zero Trust policies for workloads
- Performing MFA like checks
- Conditional access
- Integrations: Wiz and CrowdStrike
- Geolocation
Credential Providers
- Intro
- Static & ephemeral support
- GitLab CLM
Monitoring & Troubleshooting
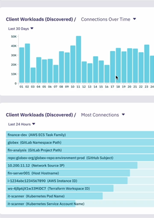
- Intro
- Dashboard view
- Reporting
- Log streams & exporting to SIEM/SOAR
Other features
- Deployment automation: Terraform & API
- Multi-tenant scenarios: Resource sets
- Secure access: SSO, MFA, and RBAC

 Play Now
Play Now